MTD technologies can increase system diversity by dynamically changing the configuration in use for different layers of the system stack. This gives attackers a random and ever-changing view of the underlying system thus increasing the difficulty of successful exploits and required effort while making persistence more challenging, and ultimately deterring them from further attacks. Deception typically employs a decoy network to entrap the attackers and divert the firepower away from the real protected assets. Recent years have witnessed a surging trend of leveraging deception techniques to detect and defeat sophisticated cyber-attacks such as the advanced persistent threat. Our group performs studies on combining MTD and deception technology and develops practical techniques to enhance the stealthiness and fidelity of deception systems.
Read more about our works:
UBER System
MIRAGE System
DESIR System

Malware analysis sandboxes have been widely used by cybersecurity teams to investigate the threat of malware. Correspondingly, malware authors have developed various anti-sandbox techniques to evade the analysis. Most of those evasion techniques are well studied and can be defeated with appropriate mitigation strategies. However, one particular technique is usually overlooked and can be extremely effective in defeating sandbox-based malware analysis, i.e., system fingerprinting. This technique leverages a variety of system artifacts that are expected to exist in a real system as a result of typical user activities for sandbox environment identification. To tackle this drawback of lacking authentic system artifacts in existing sandbox designs, in this paper we propose a novel system UBER for automatic artifact generation based on the emulation of real user behavior. It generalizes the user's computer usage pattern with an abstract behavior profile, employs the profile to guide the simulation of user actions and the generation of artifacts, and then clones the system with generated artifacts into the sandbox environment. We implement a prototype of UBER using python system-event monitor and automation control modules. The experimental results further demonstrate that UBER can generate believable system artifacts and effectively mitigate the sandbox evasion technique exploiting system fingerprinting.
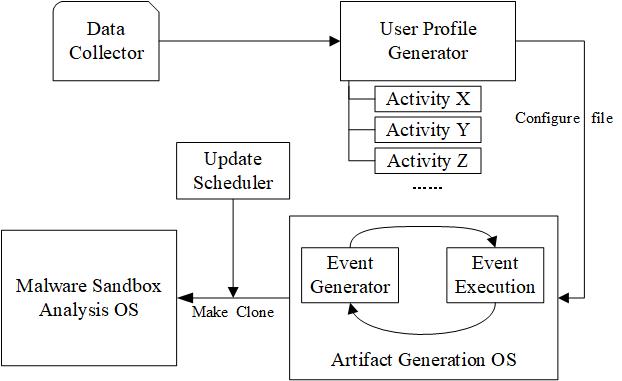
Uber System Design.
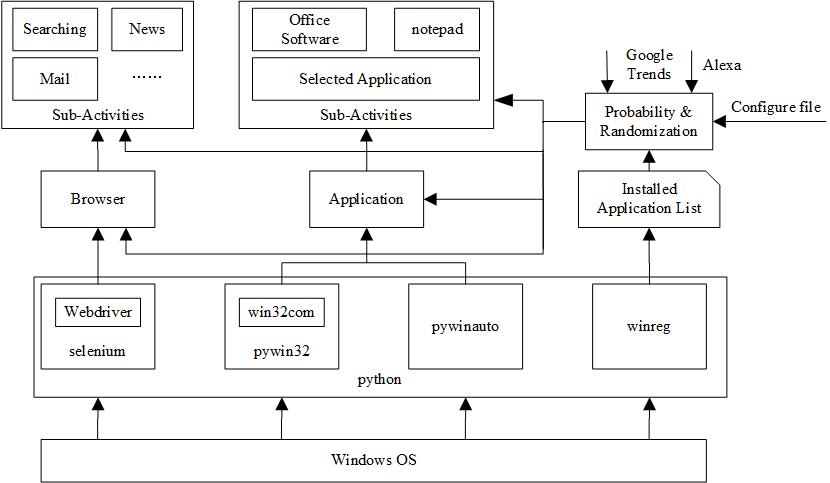
Uber System Implementation.
Published in International Conference on Information and Communications Security (ICICS) 2019.
Download the Paper Slides Code Export Citation
@inproceedings{feng2019uber,
title={UBER: Combating Sandbox Evasion via User Behavior Emulators},
author={Feng, Pengbin and Sun, Jianhua and Liu, Songsong and Sun, Kun},
booktitle={International Conference on Information and Communications Security},
pages={34--50},
year={2019},
organization={Springer}
}
By leveraging deceptive decoys, the defenders seek to proactively engage with the attackers and entice them away from the protected server infrastructure. The effectiveness of such decoy-based deception largely relies on the decoy fidelity. In this paper, we observe that realistic server system inevitably experiences wearoff from service request processing and regular maintenance, resulting in characteristic access pattern, running states, and system artifacts. Accordingly, we identify two deception evasion attacks, namely, traffic fingerprinting and system fingerprinting, which enable sophisticated adversaries to accurately distinguish decoys from real servers. To protect web server decoys against those evasion attacks, we develop Mirage, a seamless real-time network traffic replay framework to generate network traffic and system artifacts on the decoy server based on the normal clients’ interactions with the real server. Mirage works as a TLS-capable reverse proxy that transparently replays real traffic towards decoys. To resolve the inconsistent states between the real and decoy servers, we integrate a decoy client emulator into the reverse proxy to maintain the stateful data features and caching logic of a decoy session. Moreover, we employ format preserving encryption technique to obfuscate sensitive data before being sent to the decoy server. Implementations and evaluations of a prototype demonstrate that Mirage can effectively mitigate deception evasion attacks with acceptable performance overhead.
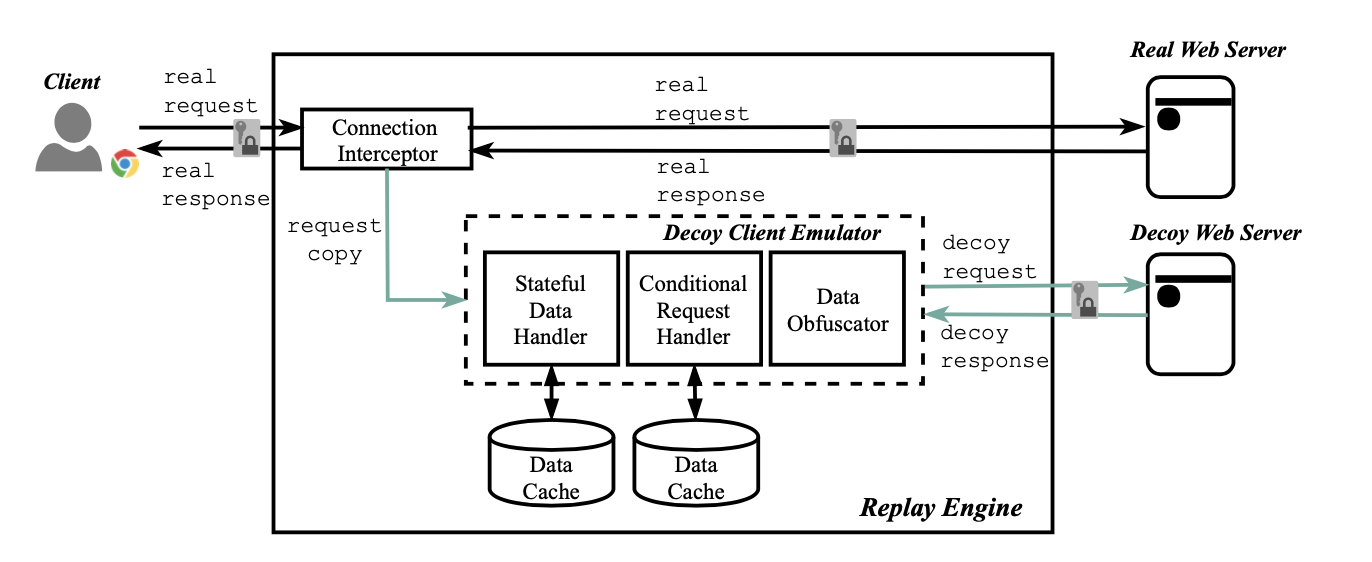
Mirage Architecture.
Published in IEEE Conference on Communications and Network Security (CNS) 2020.
Download the Paper Slides Code Export Citation
@inproceedings{sun2020mirage,
title={Towards a Believable Decoy System: Replaying Network Activities from Real System},
author={Jianhua Sun and Kun Sun and Qi Li},
booktitle={IEEE Conference on Communications and Network Security (CNS)},
year={2020}
}
To mitigate the effectiveness of persistent reconnaissance attacks, we develop a defensive mechanism that dynamically mutates network topology with a large number of decoys to invalidate the attacker’s knowledge from network scanning. We combine the IP randomization technique with decoy techniques and solve two challenges, namely, service availability to legitimate users and service security against unauthorized users. First, our solution can minimize the probability of the real servers being identified and compromised by unauthorized users through deploying a large number of decoy nodes, which change their IP addresses along with the real servers to prolong the scanning time of the attackers. Second, our solution can ensure seamless connection migration so that all existing communication connections between the legitimate users and the servers are always kept alive even after the servers migrate to different IP addresses multiple times. We implement a virtual machine based system prototype and evaluate it using state-of-the-art scanning techniques. Both theoretical analysis and experimental results show that our solution can effectively mitigate network reconnaissance attacks without sacrificing service availability.
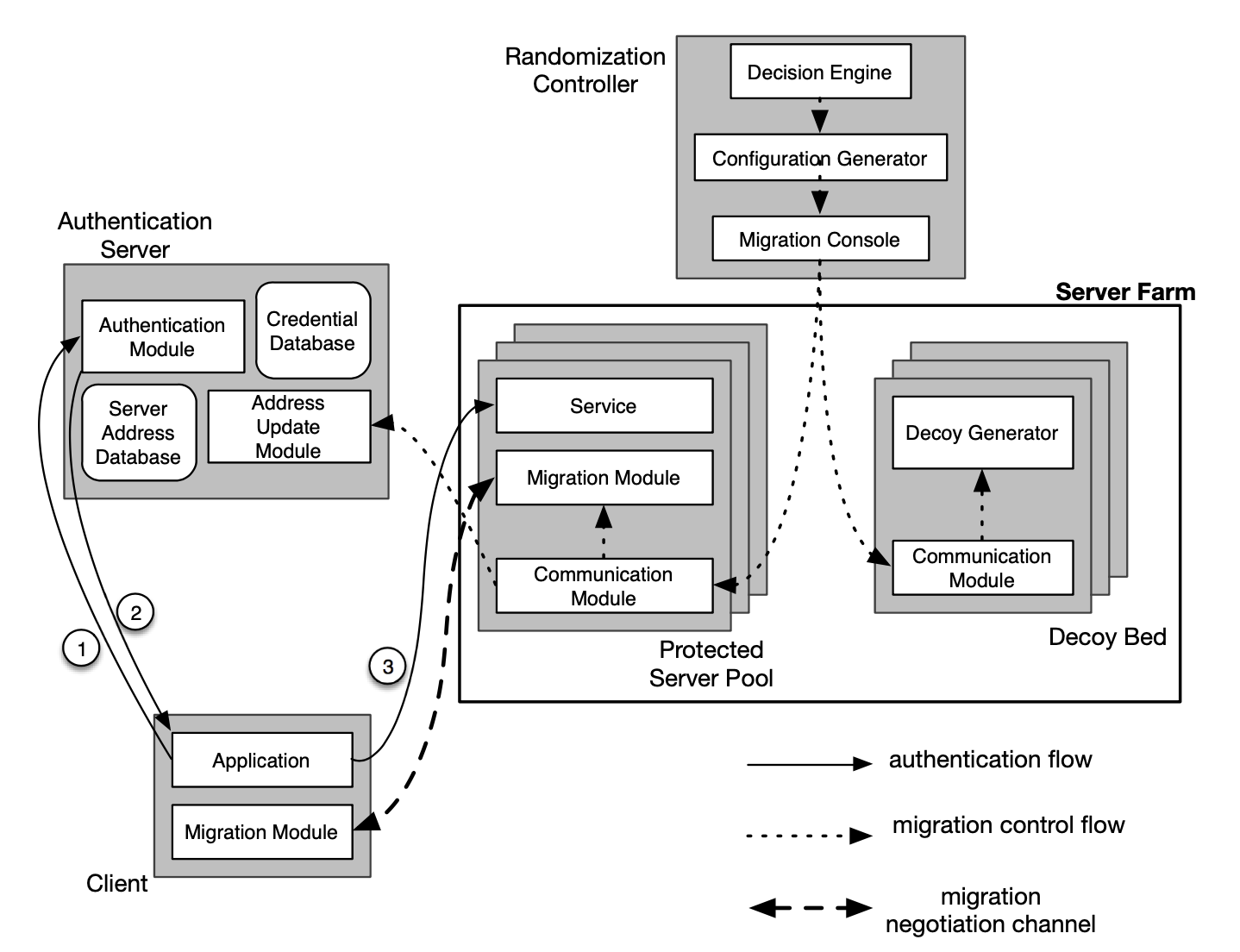
DESIR Architecture.
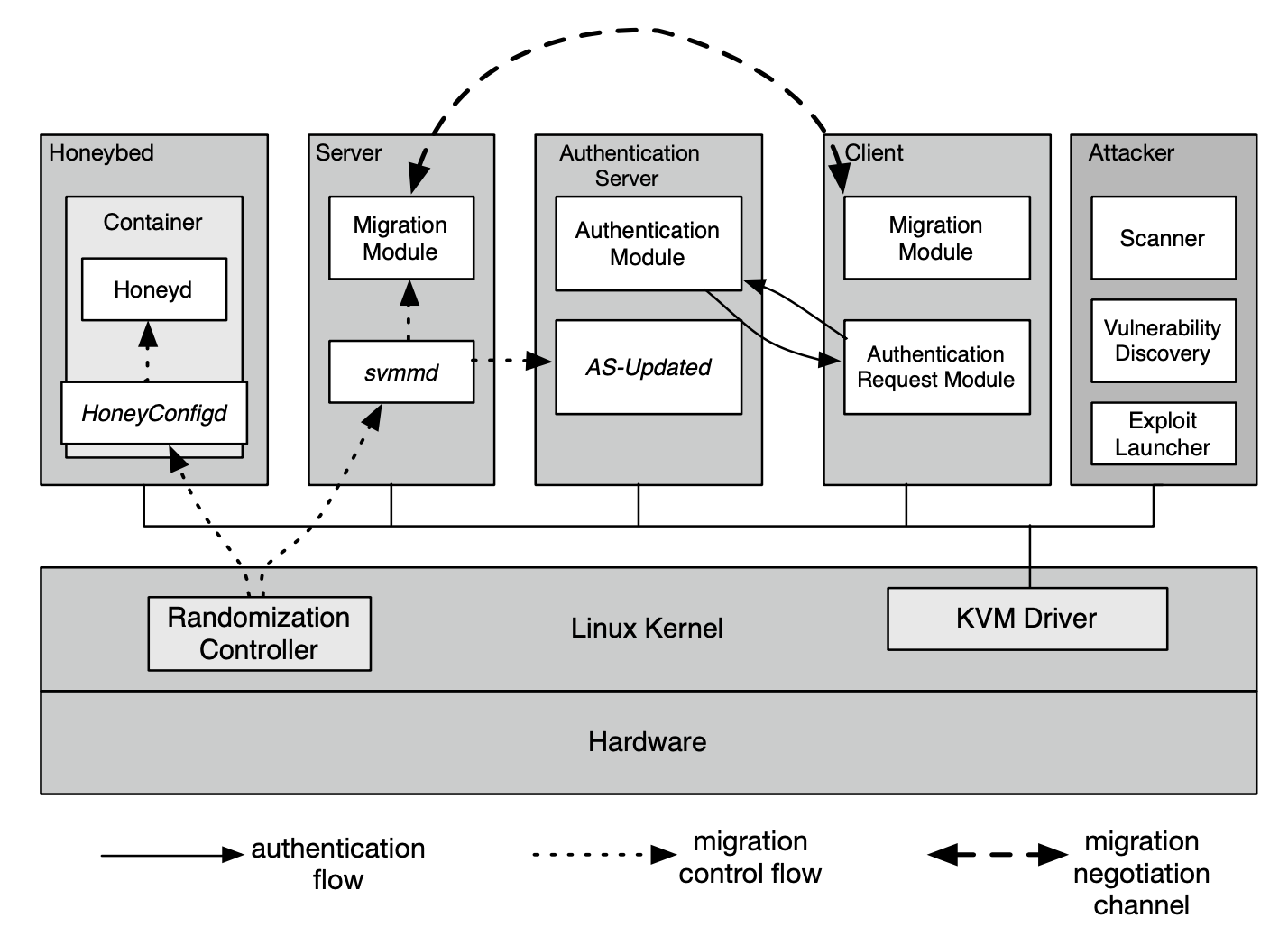
DESIR System Implementation.
Published in IEEE International Conference on Computer Communications (INFOCOM) 2016.
Download the Paper Slides Code Export Citation
@inproceedings{sun2016desir,
title={DESIR: Decoy-Enhanced Seamless IP Randomization},
author={Jianhua Sun and Kun Sun},
booktitle={IEEE International Conference on Computer Communications (INFOCOM)},
year={2016}
}