We have developed hardware-assisted secure systems on both ARM and x86 architectures since 2010. A suite of secure mechanisms has been developed to achieve isolated computing environments and dependable introspection and debugging framework. First, we tackle the secure OS isolation problem without using a hypervisor or any mutable shared code. Instead, we rely on hardware security extensions integrated on both x86 and ARM processors to achieve isolated computing environments to protect secure sensitive code and data. Second, we leverage the System Management Mode (SMM) present in the popular x86 systems and the TrustZone extension in ARM-based systems to achieve both dependable software introspection and stealthy debugging, which is critical to ensure the integrity of software stack and perform effective malware analysis, respectively.
On ARM: CITM Attack RustTEE CASE
On X86: SGX-Bouncer Malt SecureSwitch
The traditional usage of ARM TrustZone has difficulty on solving the conflicts between the manufacturers that want to minimize the trusted computing base by constraining the installation of third- party applications in the secure world and the third-party applica- tion developers who prefer to have the freedom of installing their applications into the secure world. To address this issue, researchers propose to create Isolated Execution Environments (called IEEs) in the normal world to protect the security-sensitive applications. In this paper, we perform a systematic study on the IEE data protection models and the ARM cache attributes, and discover three cache- based attacks called CITM that can be leveraged to manipulate the sensitive data protected in IEEs. Specifically, due to the inefficient and incoherent security measures on the cache that maps to the IEE memory (i.e., memory designated for IEEs), attackers in the normal world may compromise the security of IEE data by manipu- lating the IEE memory during concurrent execution, bypassing the security measures enforced when a security-sensitive application is suspended or finished, or misusing the incomplete security mea- sures during IEE’s context switching processes. We conduct case studies of CITM attacks on three well-known IEE systems including SANCTUARY, Ginseng, and TrustICE to illustrate the feasibility to exploit them on real hardware testbeds. Finally, we analyze the root causes of the CITM attacks and propose a countermeasure to defeat them. The experimental results show that our defense scheme has a small overhead.
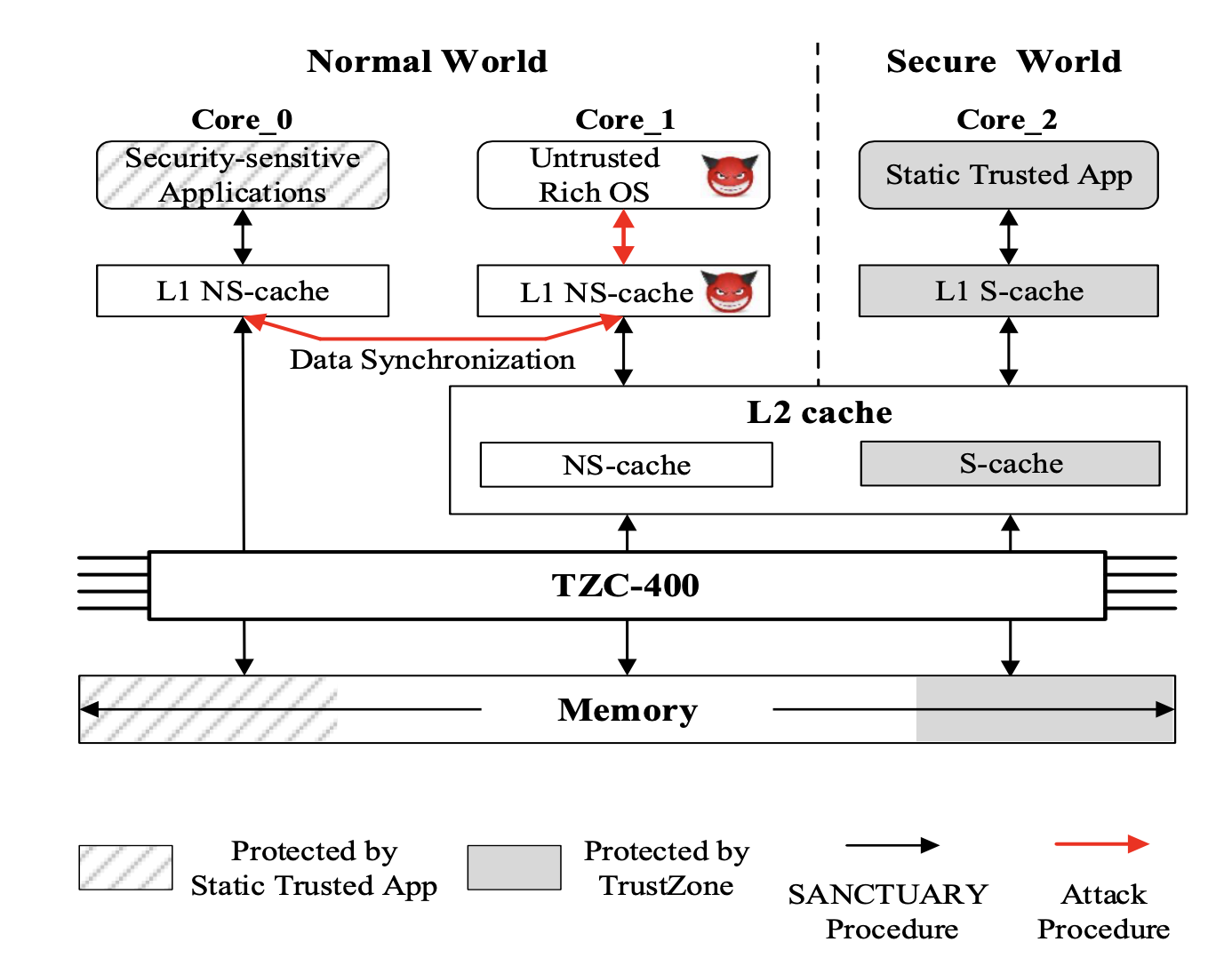
CITM Attack on SANCTUARY.
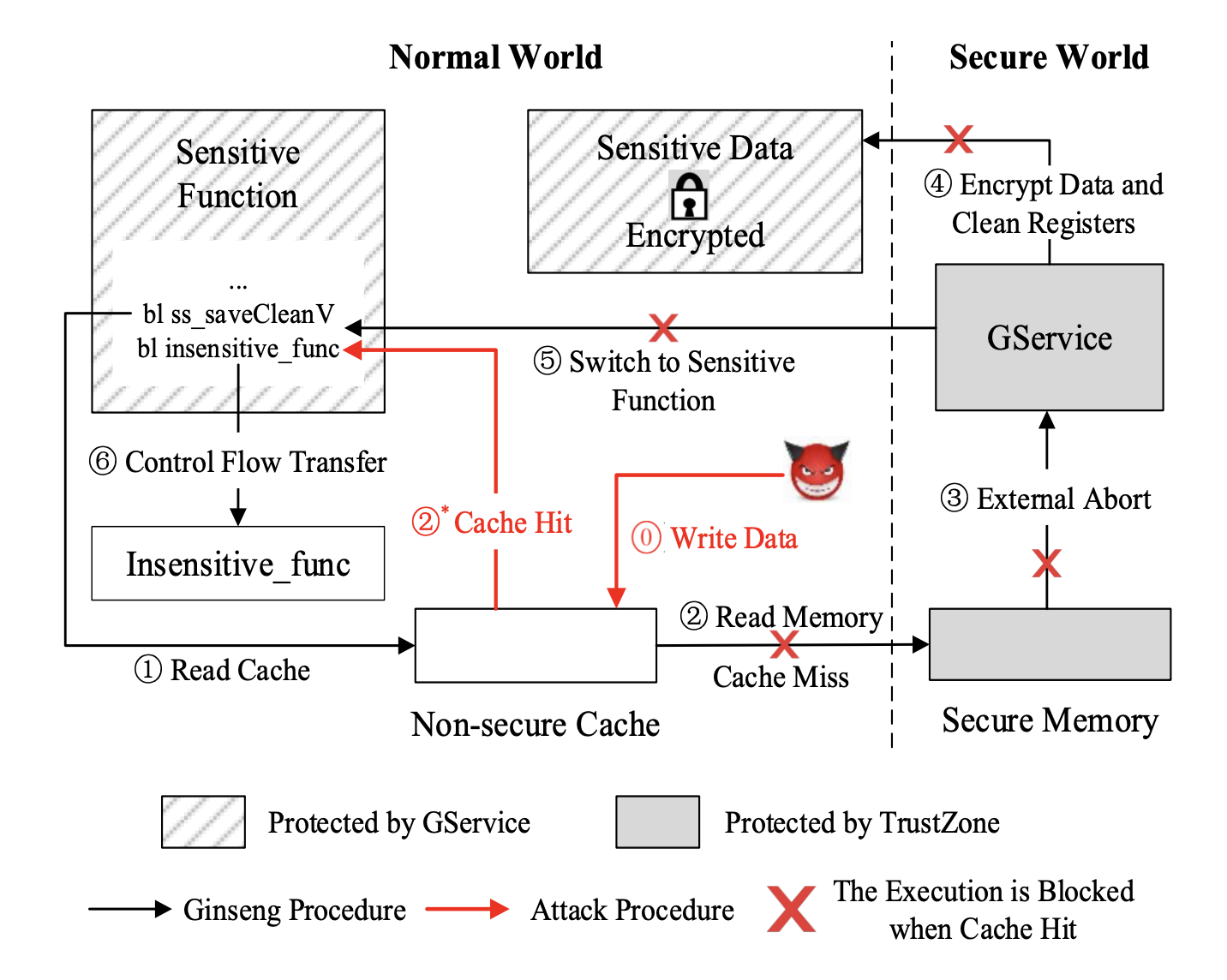
CITM Attack on Ginseng.
Published in ACM Conference on Computer and Communications Security (CCS) 2020.
Download the Paper Slides Export Citation
@inproceedings{wang2020citm,
title={Cache-in-the-Middle(CITM) Attacks: Manipulating Sensitive Data in Isolated Execution Environments.},
author={Wang, Jie and Sun, Kun and Lei, Lingguang and Wan, Shengye and Wang, Yuewu and Jing, Jiwu},
booktitle={Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security (CCS)},
location = {Virtual Event, USA},
year={2020}
}
In the past decade, Trusted Execution Environment (TEE) provided by ARM TrustZone is becoming one of the primary techniques for enhancing the security of mobile devices. The isolation enforced by TrustZone can protect the trusted applications running in the TEE against malicious software in the untrusted rich execution environment (REE). However, TrustZone cannot completely prevent vulnerabilities in trusted applications residing in the TEE, which can then be used to attack other trusted applications or even the trusted OS. Previously, a number of memory corruption vulnerabilities have been reported on different TAs, which are written in memory-unsafe languages like C. Recently, various memory-safe programming languages have emerged to mitigate the prevalent memory corruption bugs.
In this paper, we propose RusTEE, a trusted application mechanism that leverages Rust, a newly emerged memory-safe language, to enhance the security of TAs. Though the high-level idea is quite straight-forwarding, we resolve several challenges on adopting Rust in mobile TEEs. Specifically, since Rust currently does not support any TrustZone-assisted TEE systems, we extend the existing Rust compiler for providing such support. Also, we apply comprehensive security mechanisms to resolve two security issues of trusted applications, namely, securely invoking high-privileged system services and securely communicating with untrusted REE. We implement a prototype of RusTEE as the trusted applications’ SDK, which supports both emulator and real hardware devices. The experiment shows that RusTEE can compile applications with close-to-C performance on the evaluated platforms.
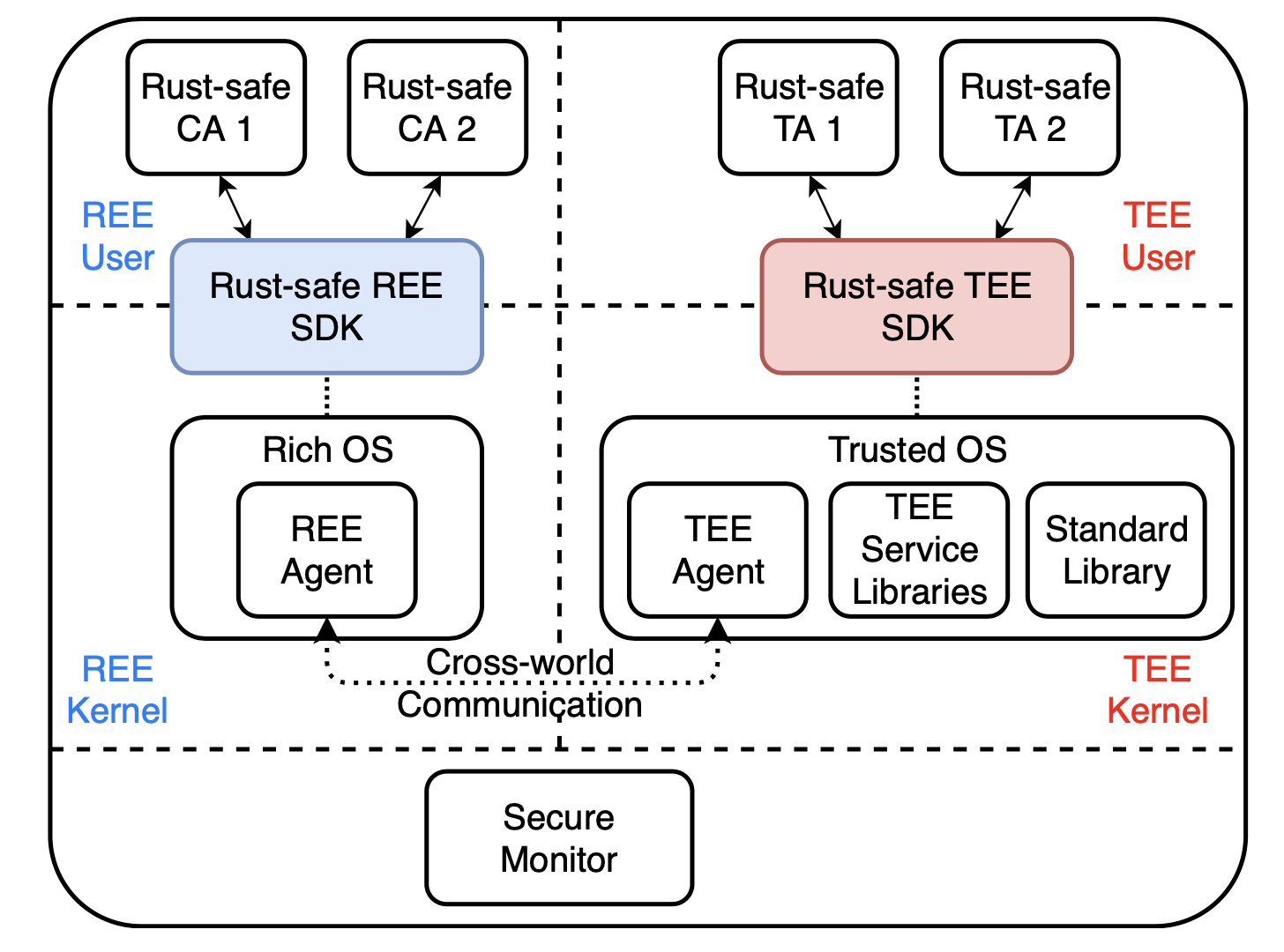
RusTEE Architecture.
Published in Annual Computer Security Applications Conference (ACSAC) 2020.
Download the Paper Slides Code Export Citation
@inproceedings{wan2020rustee,
title={RusTEE: Developing Memory-Safe ARM TrustZone Applications},
author={Wan, Shengye and Sun, Mingshen and Sun, Kun and Zhang, Ning and He, Xu},
booktitle={Annual Computer Security Applications Conference},
location = {Austin, USA},
year={2020}
}
We develop a cache-assisted secure execution mechanism called CaSE on ARM processors to defend against sophisticated attackers who can launch multi-vector attacks including software attacks and hardware memory disclosure attacks. CaSE utilizes TrustZone to create a cache based isolated execution environment, which can protect both sensitive code and data against the malicious mobile OS and the cold boot attacks. Since the encrypted secure application is loaded into the CPU cache and then decrypted within the processor, we can protect not only the sensitive data but also the code confidentiality against cold boot attacks. Moreover, we use the memory separation and the cache separation mechanism provided by TrustZone to protect the cached application against malicious mobile OS.
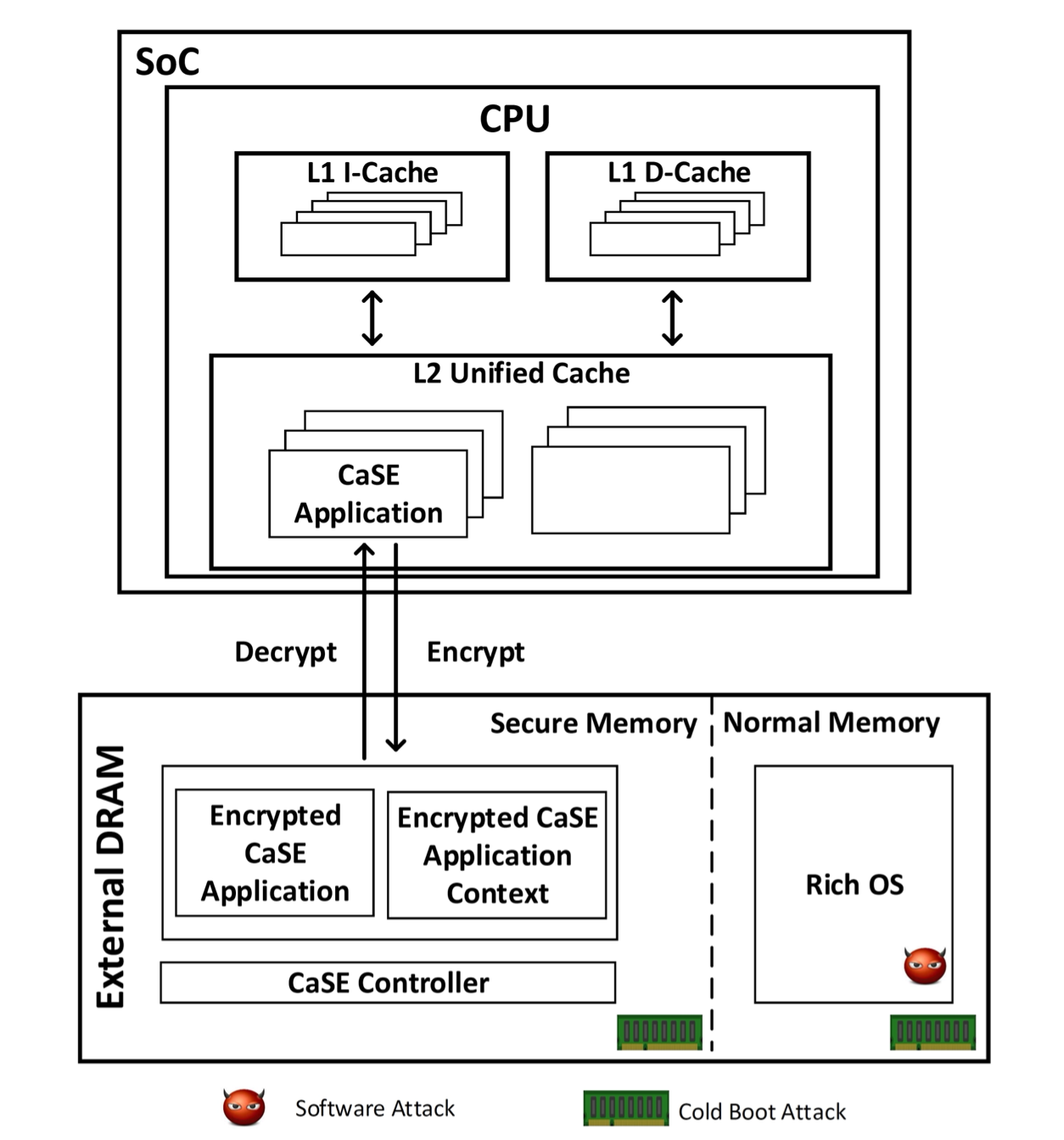
CaSE Architecture.
Published in IEEE Symposium on Security and Privacy 2016.
Download the Paper Slides Export Citation
@inproceedings{zhang2016case,
title={CaSE: Cache-Assisted Secure Execution on ARM Processors},
author={Ning Zhang, Kun Sun, Wenjing Lou, and Tom Hou},
booktitle={IEEE Symposium on Security and Privacy (SP)},
year={2016}
}
Intel software guard extensions (SGX) enables strong runtime confidentiality and integrity protection for programs and their data and has been adopted by commercial public clouds. Meanwhile, SGX may also be abused by attackers to shield their malicious behaviors in SGX enclaves. We perform a systematic study of SGX applications and formalize a comprehensive set of unwanted behaviors, including unwanted SGX development frameworks, suspicious interface behaviors, and unexpected memory access behaviors. Also, we develop a defense system that is capable of detecting various unwanted behaviors by analyzing the static binary code and runtime execution behaviors of SGX applications.
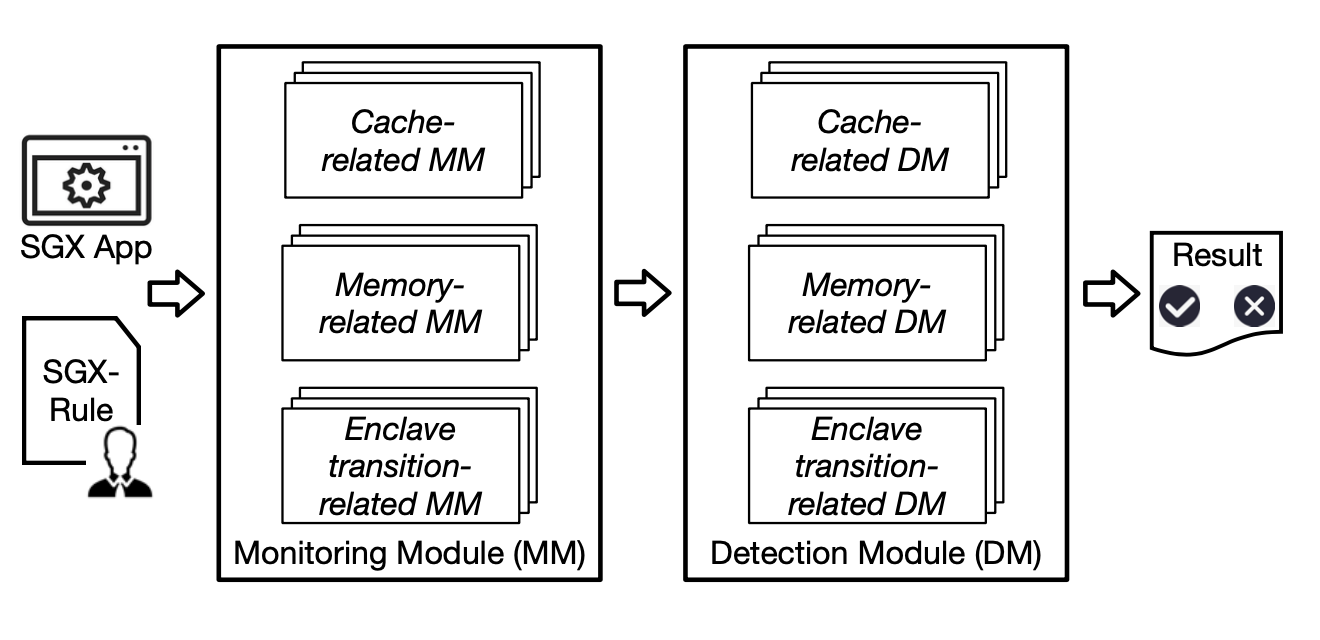
SGX-Bouncer Design.
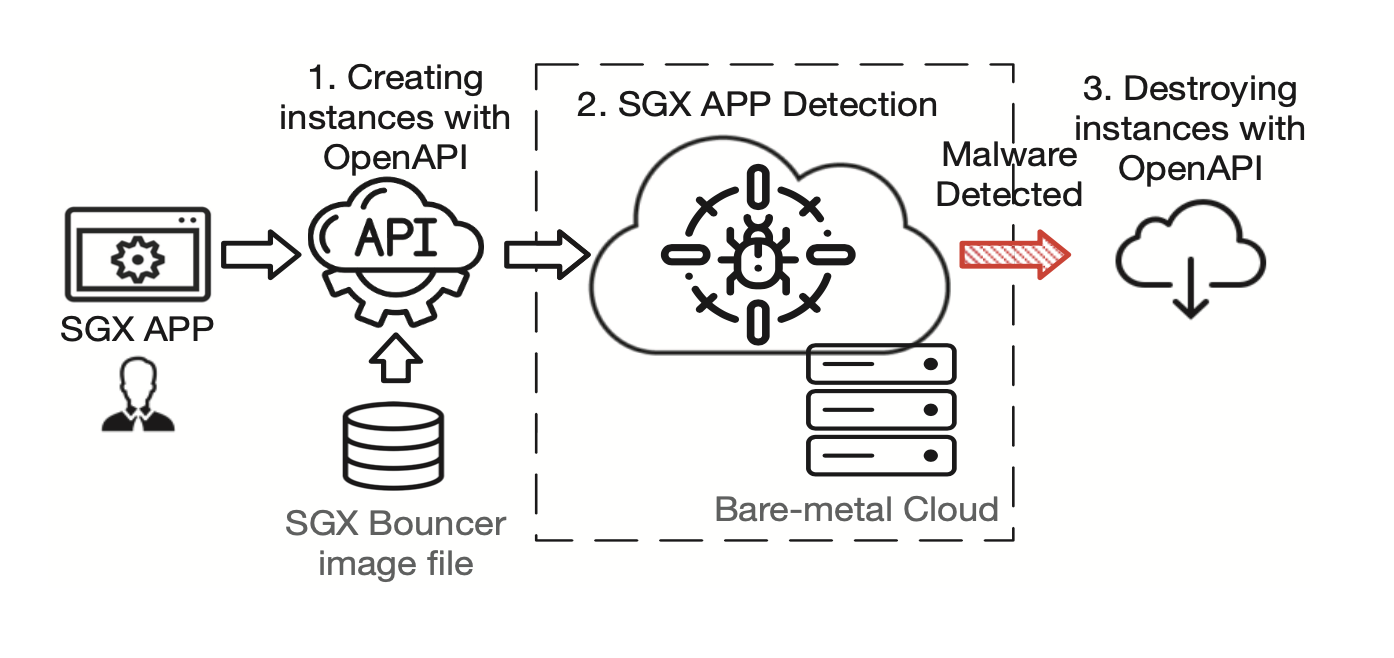
SGX-Bouncer Real-World Deployment.
Published in ACM ASIA Conference on Computer and Communications Security (ASIACCS) 2021.
Download the Paper Export Citation
@inproceedings{zhang2021sgxbouncer,
title={See through Walls: Detecting Malware in SGX Enclaves with SGX-Bouncer},
author={Zeyu Zhang, Xiaoli Zhang, Qi Li, Kun Sun, Yinqian Zhang, SongSong Liu, Yukun Liu, and Xiaoning Li,},
booktitle={ACM Asia Conference on Computer and Communications Security (ASIACCS)},
year={2021}
}
We develop a novel approach that progresses towards stealthy debugging by leveraging SMM to transparently debug software without depending upon virtualization technology. Our approach reduces the attack surface at the software level and advances state-of-the-art debugging transparency. It embodies various debugging functions, including register/memory accesses, breakpoints, and four stepping modes. We implement a prototype on two physical machines, and the experimental results show that our prototype remains transparent and undetected against an array of existing anti-virtualization, anti-emulation, and packing techniques. Furthermore, our prototype introduces moderate but manageable overheads on both Windows and Linux platforms.
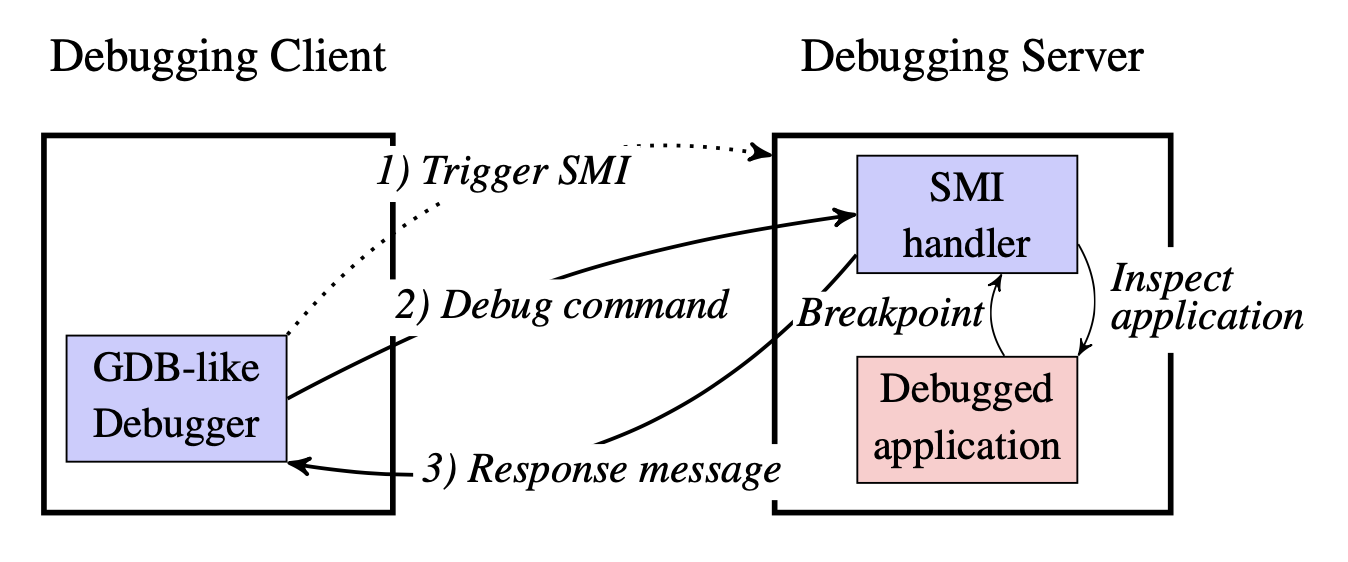
Malt Architecture.
Published in IEEE Symposium on Security and Privacy 2015.
Download the Paper Slides Export Citation
@inproceedings{zhang2015malt,
title={Using Hardware Features for Increased Debugging Transparency},
author={Fengwei Zhang, Kevin Leach, Angelos Stavrou, Haining Wang, and Kun Sun},
booktitle={IEEE Symposium on Security and Privacy},
year={2015}
}
We design a firmware-assisted system called SecureSwitch on x86 architecture, which allows users to switch between a trusted operating system and an untrusted operating system on the same physical machine with a short switching time. The basic input/output system (BIOS) is the only trusted computing base that ensures the resource isolation and enforces a trusted path for switching between the two OSes. If the untrusted OS has been compromised, it still cannot read, write, or execute any of the data and applications in the trusted OS. In our prototype, the entire switching process takes approximately 6 seconds on average.
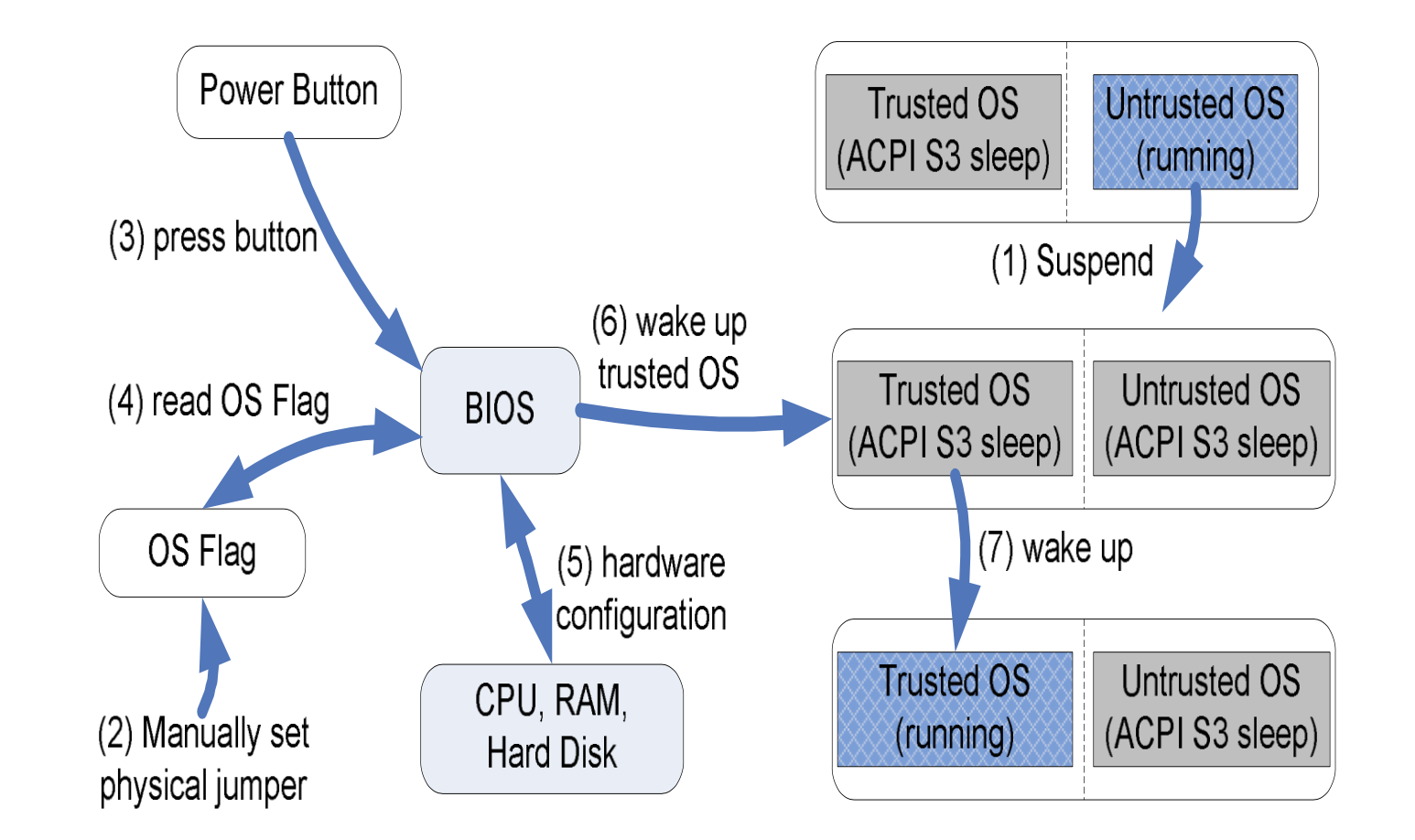
Switching Flow from Untrusted OS to Trusted OS.
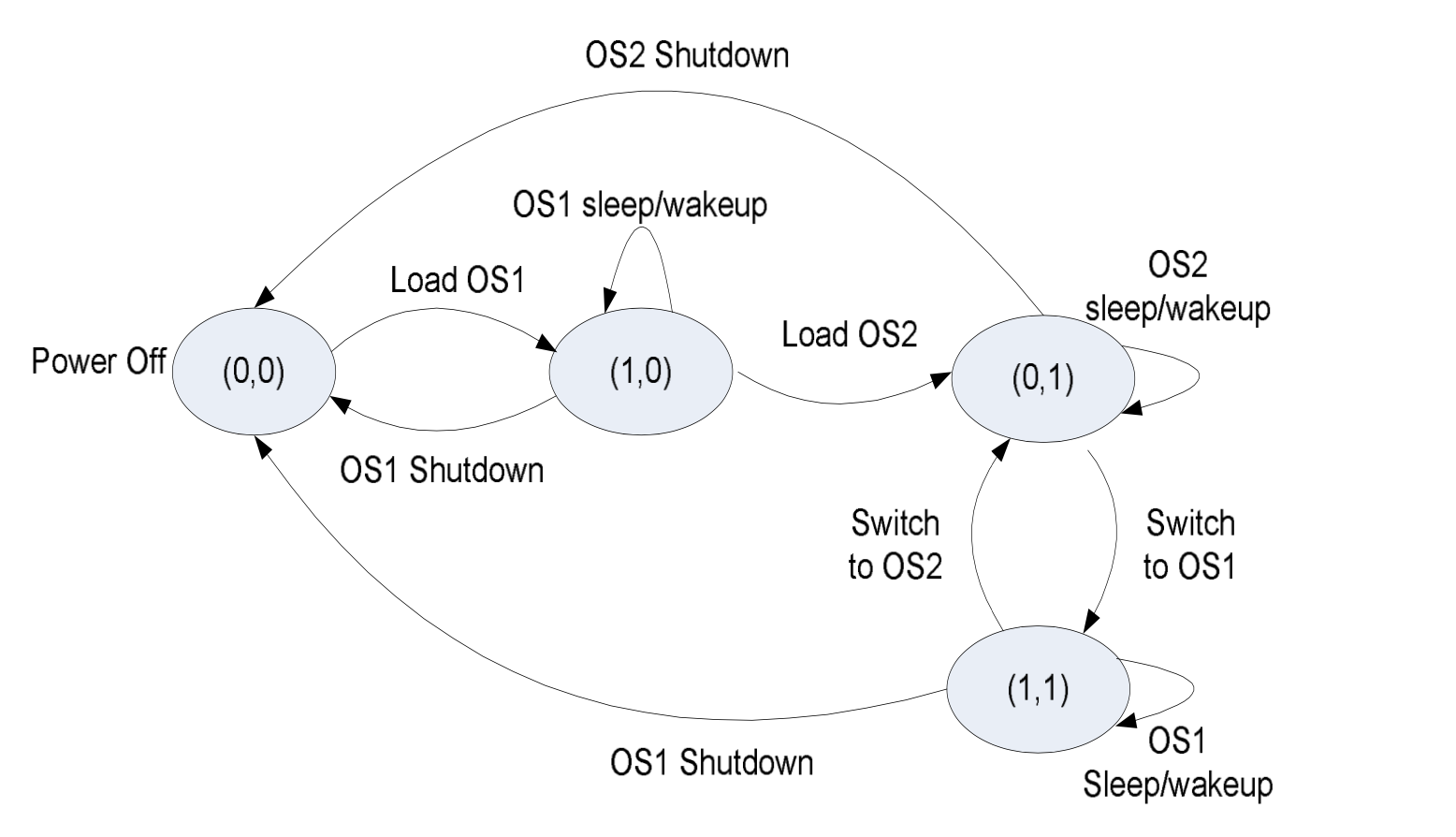
State Machine for OS Switching.
Published in The Network and Distributed System Security Symposium (NDSS) 2012.
Download the Paper Slides Export Citation
@inproceedings{sun2012secureswitch,
title={SecureSwitch: BIOS-Assisted Isolation and Switch between Trusted and Untrusted Commodity OSes},
author={Kun Sun, Jiang Wang, Fengwei Zhang, and Angelos Stavrou},
booktitle={Annual Network & Distributed System Security Symposium (NDSS)},
year={2012}
}