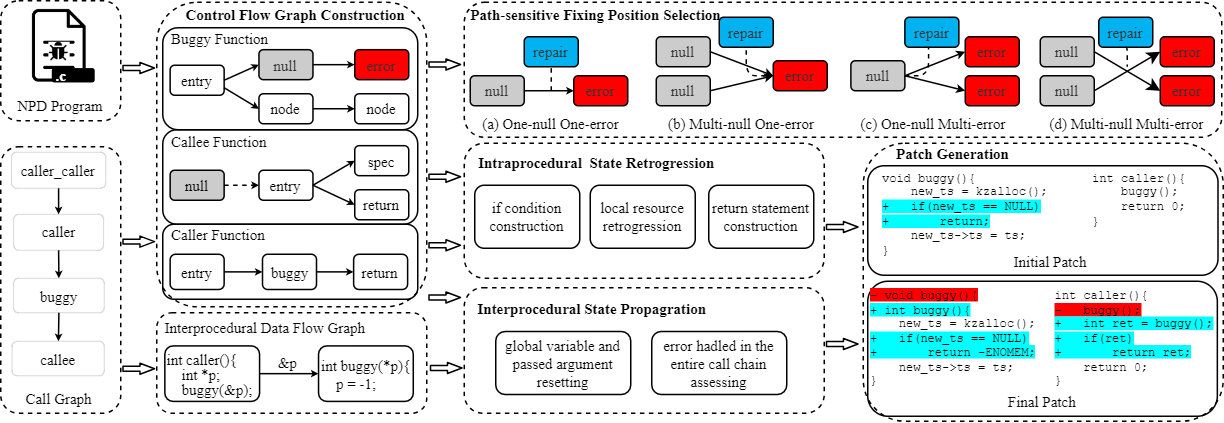
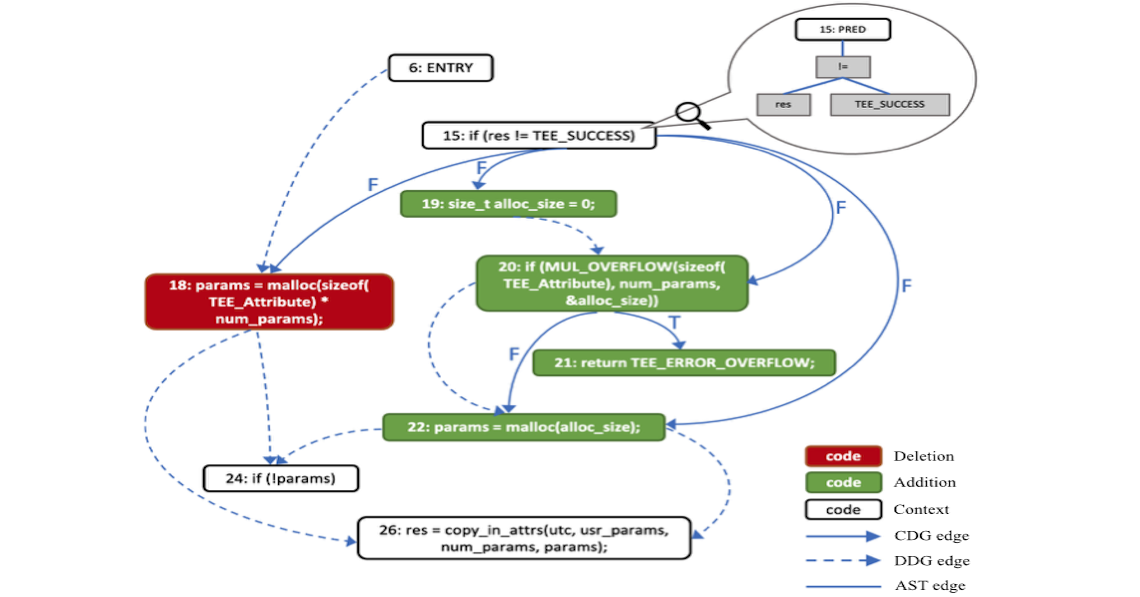
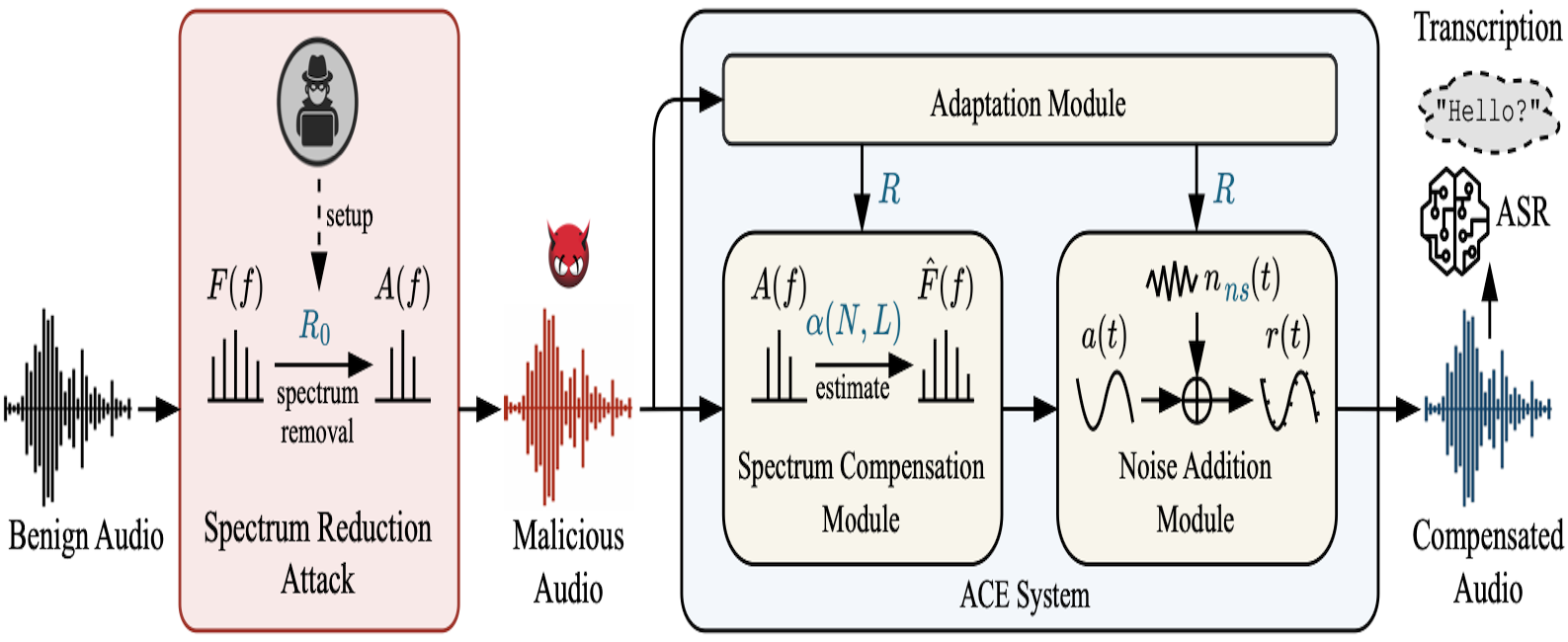
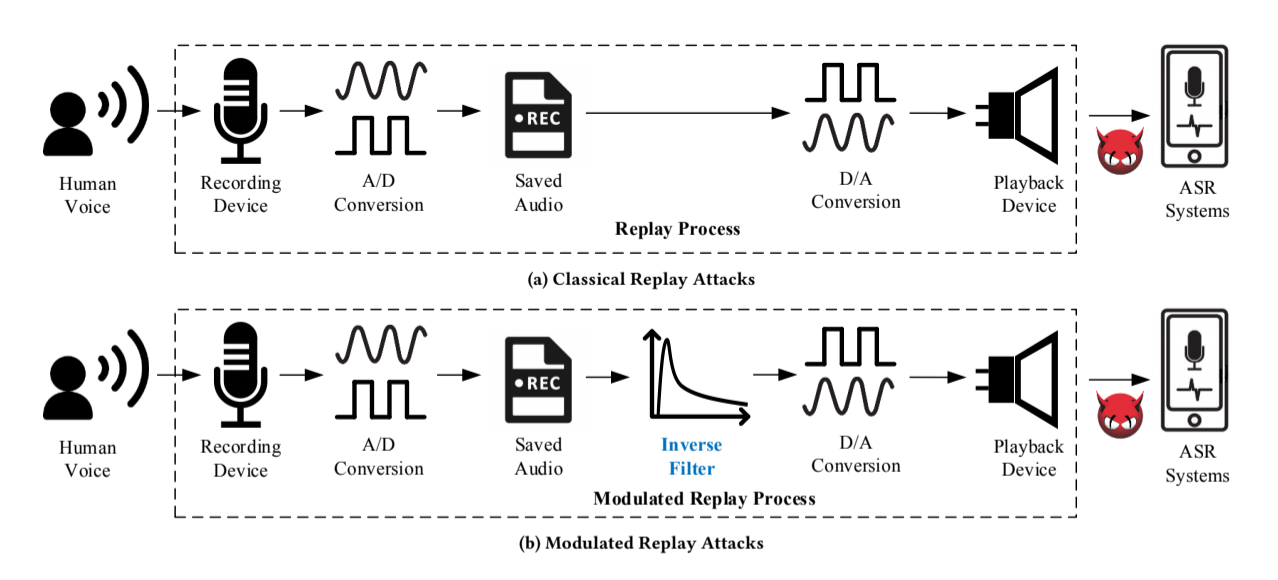
publication
Yuqi Qing, Qilei Yin, Xinhao Deng, Xiaoli Zhang, Peiyang Li, Zhuotao Liu, Kun Sun, Ke Xu, and Qi Li.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS).
Taiper, Taiwan, October 13 - October 17, 2025.
Xuewei Feng, Zhaoxi Li, Qi Li, Ziqiang Wang, Kun Sun, and Ke Xu.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS).
Taiper, Taiwan, October 13 - October 17, 2025.
Hung Mao Chen, Xu He, Shu Wang, Xiaokuan Zhang, and Kun Sun.
To appear in the 34th USENIX Security Symposium (USENIX Security'25).
Seattle, WA, August 13 - August 18, 2025.
Shiyu Sun, Yunlong Xing, Xinda Wang, Shu Wang, Qi Li, and Kun Sun.
To appear in the 34th USENIX Security Symposium (USENIX Security'25).
Seattle, WA, August 13 - August 18, 2025.
Shiyu Sun, Yunlong Xing, Grant Zou, Xinda Wang, and Kun Sun.
To appear in the In 22nd Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA).
Austria, July 9 - July 11, 2025.
Xuewei Feng, Yuxiang Yang, Qi Li, Xingxiang Zhan, Kun Sun, Ziqiang Wang, Ao Wang,Ganqiu Du, and Ke Xu.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, CA, February 23 - February 28, 2025.
Ziqiang Wang, Xuewei Feng, Qi Li, Kun Sun, Yuxiang Yang, Mengyuan Li, Ganqiu Du, Ke Xu, and Jianping Wu.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, CA, February 23 - February 28, 2025.
Shu Wang, Kun Sun, and Yan Zhai.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS).
Salt Lake City, UT, October 14-18, 2024.
Xijia Che, Yi He, Xuewei Feng, Kun Sun, Ke Xu, and Qi Li.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS).
Salt Lake City, UT, October 14-18, 2024.
Xiyuan Zhao, Xinhao Deng, Qi Li, Yunpeng Liu, Zhuotao Liu, Kun Sun, and Ke Xu.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS).
Salt Lake City, UT, October 14-18, 2024.
Shengye Wan, Joshua Saxe, Craig Gomes, Sahana Chennabasappa, Avilash Rath, Kun Sun, and Xinda Wang.
The 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN).
Brisbane, Australia, June 24-27, 2024.
Ye Wang, Yunpeng Liu, Ningtao Wang, Peiyang Li, Jiahao Hu, Xing Fu, Weiqiang Wang, Kun Sun, Qi Li, and Ke Xu.
To appear in the IEEE/ACM International Symposium on Quality of Service (IWQOS).
Guangzhou, China, 19–21 June 2024.
Xu He, Shu Wang, Pengbin Feng, Xinda Wang, Shiyu Sun, Qi Li, and Kun Sun.
To appear in the 19th ACM ASIA Conference on Computer and Communications Security (ASIACCS).
Singapore, 1-5 July, 2024.
Songsong Liu, Shu Wang, and Kun Sun.
To appear in the 16th ACM SIGCHI Symposium on Engineering Interactive Computing Systems (EICS).
Cagliari, Italy, 24-28 June 2024.
Yunlong Xing, Shu Wang, Shiyu Sun, Xu He, Kun Sun and Qi Li.
To appear in the 33rd USENIX Security Symposium (USENIX Security'24).
Philadelphia, PA, August 14–16, 2024.
Yuhao Wu, Jinwen Wang, Yujie Wang, Shixuan Zhai, Zihan Li, Yi He, Kun Sun, Qi Li, and Ning Zhang.
To appear in the 33rd USENIX Security Symposium (USENIX Security'24).
Philadelphia, PA, August 14–16, 2024.
Tommy Chin, Noah Korzak, and Kun Sun.
To appear in the Proceedings of the 10th ACM Workshop on Moving Target Defense (MTD), in conjunction with the ACM Conference on Computer and Communications Security (ACM CCS 2023).
Copenhagen, Denmark, November 26, 2023.
Shu Wang, Kun Sun, and Qi Li.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, California, February 26-March 1, 2024.
Shiqing Luo, Anh Nguyen, Hafsa Farooq, Kun Sun, and Zhisheng Yan.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, California, February 26-March 1, 2024.
Yue Xiao, Yi He, Xiaoli Zhang, Qian Wang, Renjie Xie, Kun Sun, Ke Xu, and Qi Li.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, California, February 26-March 1, 2024.
Yuxiang Yang, Xuewei Feng, Qi Li, Kun Sun, Ziqiang Wang, and Ke Xu.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, California, February 26-March 1, 2024.
Yuqi Qing, Qilei Yin, Xinhao Deng, Yihao Chen, Zhuotao Liu, Kun Sun, Ke Xu, Jia Zhang, and Qi Li.
To appear in the Network and Distributed System Security Symposium (NDSS).
San Diego, California, February 26-March 1, 2024.
Shouyin Xu, Yuewu Wang, Lingguang Lei, Kun Sun, Jiwu Jing, Siyuan Ma, Jie Wang, and Heqing Huang.
To appear in the IEEE Transactions on Information Forensics and Security (TIFS), 2024.
Fan Zhou, Dongxia Wang, Yanhai Xiong, Kun Sun, and Wenhai Wang.
To appear in Computers & Security, 2024.
Yunlong Xing, Xinda Wang, Sadegh Torabi, Zeyu Zhang, Lingguang Lei, and Kun Sun.
To appear in the Transactions on Dependable and Secure Computing (TDSC), 2023.
Jie Wang, Kun Sun, Lingguang Lei, Yuewu Wang, Jiwu Jing, Shengye Wan, and Qi Li.
To appear in the Transactions on Dependable and Secure Computing (TDSC), 2023.
Xiaohan Zhang, Jinwen Wang, Yueqiang Cheng, Qi Li, Kun Sun, Yao Zheng, Ning Zhang, and Xinghua Li.
To appear in IEEE/ACM Transactions on Networking (TON), 2023.
Songsong Liu, Shu Wang, and Kun Sun.
To appear in the 53rd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Track of Disruptive Idea
Porto, Portugal, June 27-30, 2023.
Yi He, Roland Guo, Yunlong Xing, Xijia Che, Kun Sun, Zhuotao Liu, Ke Xu, and Qi Li.
To appear in 32nd USENIX Security Symposium (USENIX Security'23).
ANAHEIM, CA, USA, August 9–11, 2023.
Renjie Xie, Jiahao Cao, Enhuan Dong, Mingwei Xu, Kun Sun, Qi Li, Licheng Shen, and Menghao Zhang.
To appear in 32nd USENIX Security Symposium (USENIX Security'23)
ANAHEIM, CA, USA, August 9–11, 2023.
Shu Wang, Xinda Wang, Kun Sun, Sushil Jajodia, Haining Wang, and Qi Li.
To appear in the 44th IEEE Symposium on Security and Privacy (IEEE S&P)
SAN FRANCISCO, CA, MAY 22-26, 2023.
Xuewei Feng, Qi Li, Kun Sun, Yuxiang Yang, and Ke Xu.
To appear in the 44th IEEE Symposium on Security and Privacy (IEEE S&P)
SAN FRANCISCO, CA, MAY 22-26, 2023.
Shiyu Sun, Shu Wang, Xinda Wang, Yunlong Xing, Elisa Zhang, and Kun Sun.
To appear in the 39th IEEE International Conference on Software Maintenance and Evolution (ICSME)
Bogotá, Colombia, October 1-6, 2023.
Yunlong Xing, Jiahao Cao, Xinda Wang, Sadegh Torabi, Kun Sun, Fei Yan, and Qi Li.
In IEEE Conference on Communications and Network Security (CNS)
Austin, TX and virtually on October 3-5, 2022.
Guannan Liu, Daiping Liu, Shuai Hao, Xing Gao, Kun Sun, and Haining Wang.
To appear in the Proceedings of ACM Conference on Computer and Communications Security (CCS)
Los Angeles, CA, November 7-11, 2022.
Yuan Liang, Xing Gao, Kun Sun, Wenjie Xiong, and Haining Wang.
To appear in the 41st International Symposium on Reliable Distributed Systems (SRDS)
Vienna, Austria, September 19-22, 2022.
Xu He, Shu Wang, Yunlong Xing, Pengbin Feng, Haining Wang, Qi Li, Songqing Chen, and Kun Sun.
To appear in the 25th International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2022)
Limassol, Cyprus on 26-28 October, 2022.
Songsong Liu, Pengbin Feng, Jiahao Cao, Xu He, Tommy Chin, Kun Sun, and Qi Li.
To appear in the 19th Conference on Detection of Intrusions and Malware \& Vulnerability Assessment (DIMVA)
Cagliari, Italy June 29 – July 1, 2022.
Jiahao Cao, Mingwei Xu, Qi Li, Kun Sun, and Yuan Yang.
To appear in IEEE/ACM Transactions on Networking (TON), 2022.
Yunlong Xing, Jiahao Cao, Kun Sun, Fei Yan, and Shengye Wan.
Future Generation Computer Systems (FGCS), 2022.
Zili Zha, An Wang, Yang Guo, Qun Li, Kun Sun, and Songqing Chen.
To appear in the IFIP Networking Conference.
Catania Italy, June 13-16, 2022.
Xuewei Feng, Qi Li, Kun Sun, Zhiyun Qian, Chuanpu Fu, Gang Zhao, Xiaohui Kuang, and Ke Xu.
To appear in 31st USENIX Security Symposium (USENIX Security'22)
BOSTON, MA, USA, August 10–12, 2022.
Yi He, Zhenhua Zou, Kun Sun, Zhuotao Liu, Ke Xu, Qian Wang, Chao Shen, Zhi Wang, and Qi Li.
To appear in 31st USENIX Security Symposium (USENIX Security'22)
BOSTON, MA, USA, August 10–12, 2022.
Guannan Liu, Xing Gao, Haining Wang, and Kun Sun
To appear in 31st USENIX Security Symposium (USENIX Security'22)
BOSTON, MA, USA, August 10–12, 2022.
Xuewei Feng, Qi Li, Kun Sun, Ke Xu, Baojun Liu, Xiaofeng Zheng, Qiushi Yang, Haixin Duan, and Zhiyun Qian.
To appear in the Network and Distributed System Security Symposium (NDSS)
San Diego, CA, February 27- March 3, 2022.
Xin Tan, Yuan Zhang, Jiajun Cao, Kun Sun, Mi Zhang and Min Yang
To appear in the Proceedings of 31st ACM Web Conference (WWW)
Virtual Event, Lyon, France, April 25–29, 2022.
Xu He, Jiahao Cao, Shu Wang, Kun Sun, Lisong Xu, and Qi Li.
To appear in IEEE International Conference on Computer Communications (INFOCOM)
London, United Kingdom, May 2-5, 2022. Virtual Conference.
Songsong Liu, Pengbin Feng, Shu Wang, Kun Sun, and Jiahao Cao
To appear in Computers & Security, 2022
Zijie Yang, Jiahao Cao, Zhuotao Liu, Kun Sun, and Qi Li
To appear in the IEEE Transactions on Information Forensics and Security (TIFS), 2022
Yi He,Yacong Gu, Purui Su, Kun Sun, Zhi Wang, Yajin Zhou, and Qi Li
To appear in the Transactions on Dependable and Secure Computing (TDSC), 2022
Renjie Xie, Jiahao Cao, Qi Li, Kun Sun, Guofei Gu, Mingwei Xu, and Yuan Yang
To appear in IEEE/ACM Transactionson Networking (TNET), 2022.
Feng, Xuewei; Li, Qi; Sun, Kun; Fu, Chuanpu; Xu, Ke
To appear in IEEE/ACM Transactions on Networking, 2021
Xinda Wang, Shu Wang, Pengbin Feng, Kun Sun, Sushil Jajodia, Sanae Benchaaboun, and Frank Geck
Military Communications Conference (MILCOM)
San Diego, CA, USA, 29 November–2 December 2021.
Songsong Liu, Pengbin Feng, and Kun Sun
In IEEE Conference on Communications and Network Security (CNS)
Virtual Conference, October 4-6, 2021
Qiyang Song, Jiahao Cao, Kun Sun, Qi Li, and Ke Xu
To appear in Annual Computer Security Applications Conference (ACSAC)
Virtual Conference, December 6-10, 2021
Jiaming Mu, Binghui Wang, Qi Li,Kun Sun, Mingwei Xu, and Zhuotao Liu
To appear in ACM Conference on Computer and Communications Security (CCS)
Seoul, South Korea, November 14-19, 2021.
Xin Tan, Yuan Zhang, Chenyuan Mi, Jiajun Cao, Kun Sun, Yifan Lin, and Min Yang
To appear in ACM Conference on Computer and Communications Security (CCS)
Seoul, South Korea, November 14-19, 2021.
Shengye Wan, Kun Sun, Ning Zhang, and Yue Li
To appear in 14th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec)
Virtual Event, November 14-19, 2021.
Xinda Wang, Shu Wang, Pengbin Feng, Kun Sun, and Sushil Jajodia
To appear in the 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks(DSN)
Taibei, Taiwan, June 21-24, 2021.
[Paper]
Yue Li, Zhenyu Wu, Haining Wang, Kun Sun, Zhichun Li, Kangkook Jee, Junghwan Rhee, and Haifeng Chen
To appear in the 11th ACM Conference on Data and Application Security and Privacy (CODASPY)
April 26 - 28, 2021. Taking place virtually.
[Paper]
Fengting Li, Xuankai Liu, Xiaoli Zhang, Qi Li, Kun Sun, and Kang Li
To appear in the IEEE International Conference on Computer Communications (INFOCOM)
10-13 May 2021. Virtual Conference.
[Paper]
Zeyu Zhang, Xiaoli Zhang, Qi Li, Kun Sun, Yinqian Zhang, SongSong Liu, Yukun Liu, and Xiaoning Li
To appear in The ACM Asia Conference on Computer and Communications Security (ACM ASIACCS)
Hong Kong, China, June 7-11, 2021
Acceptance ratio: 18.47%=29/157
[Paper]
Jie Wang, Yuewu Wang, Lingguang Lei, Kun Sun, Jiwu Jing, and Quan Zhou
To appear in the 18th ACM Conference on Embedded Networked Sensor Systems (SenSys)
Yokohama, Japan November 16-19, 2020
[Paper]
Shengye Wan, Mingshen Sun, Kun Sun, Ning Zhang, and Xu He
To appear in Annual Computer Security Applications Conference (ACSAC)
Austin, Texas, USA, December 7-11, 2020
[Paper]
Yifei Wu, Lingguang Lei, Yuewu Wang, Kun Sun, and Jingzi Meng
To appear in the 23th Information Security Conference (ISC)
Bali, Indonesian, December 16-19, 2020
Acceptance ratio: 25.50%=23/90
[Paper]
Jie Wang, Kun Sun, Lingguang Lei, Shengye Wan, Yuewu Wang, and Jiwu Jing
To appear in ACM Conference on Computer and Communications Security (CCS)
Orlando, USA, November 9-13, 2020
[Paper]
Xuewei Feng, Chuanpu Fu, Qi Li, Kun Sun, and Ke Xu
To appear in ACM Conference on Computer and Communications Security (CCS)
Orlando, USA, November 9-13, 2020
[Paper]
Shu Wang, Jiahao Cao, Xu He, Kun Sun, and Qi Li
To appear in ACM Conference on Computer and Communications Security (CCS)
Orlando, USA, November 9-13, 2020
[Paper]
Songsong Liu, Qiyang Song, Kun Sun, and Qi Li
To appear in the 16th EAI International Conference on Security and Privacy in Communication Networks (SecureComm)
Washington D.C., USA, October 21-23, 2020
[Paper]
Shu Wang, Jiahao Cao, Kun Sun, and Qi Li
To appear in the International Symposium on Research in Attacks, Intrusions and Defenses (RAID)
Donostia/San Sebastian, Spain, October 14-16, 2020
Acceptance ratio: 24.79%=31/121
[Paper]
Yi He, Yuan Zhou, Yajin Zhou, Qi Li, Kun Sun, Yacong Gu, and Yong Jiang
To appear in the Transactions on Dependable and Secure Computing (TDSC)
2020
[pdf]
Xinda Wang, Shu Wang, Kun Sun, Archer Batcheller, and Sushil Jajodia
To appear in IEEE Conference on Communications and Network Security (CNS)
Virtual Conference, 29 June – 1 July 2020
[Paper]
Jianhua Sun, Kun Sun, and Qi Li
To appear in IEEE Conference on Communications and Network Security (CNS)
Virtual Conference, 29 June – 1 July 2020
[Paper]
Yue Li, Zeyu Chen, Haining Wang, Kun Sun, and Sushil Jajodia
To appear in the Transactions on Dependable and Secure Computing (TDSC)
2020
[pdf]
Jiahao Cao, Renjie Xie, Kun Sun, Qi Li, Guofei Gu, and Mingwei Xu
To appear in the Network and Distributed System Security Symposium (NDSS)
San Diego, CA, February 23-26, 2020
[Paper]
Pengbin Feng, Jianhua Sun, Songsong Liu, and Kun Sun
Proceedings of the 21st International Conference on Information and Communications Security (ICICS)
Beijing, China, December 15-17, 2019
Acceptance ratio: 23.6%=47/199
[Paper]
Isabelle Choi, Qiyang Song, and Kun Sun
Proceedings of the 2019 IEEE Conference on Dependable and Secure Computing (DSC)
Hangzhou, China, November 18-20, 2019.
Jianhua Sun, Songsong Liu, and Kun Sun
Proceedings of the 6th ACM Workshop on Moving Target Defense (MTD) in conjunction with the 26th ACM Conference on Computer and Communications Security (ACM CCS)
London, UK, November 11, 2019
[Paper]
Huan Chang, Lingguang Lei, Kun Sun, Yuewu Wang, Jiwu Jing, Yi He, and Pingjian Wang
To appear in IEEE Transactions on Dependable and Secure Computing (TDSC)
Dawei Chu, Yuewu Wang, Lingguang Lei, Yanchu Li, Jiwu Jing, and Kun Sun
In the European Symposium on Research in Computer Security (ESORICS)
Luxembourg, September 23-27, 2019
Acceptance ratio: 19.5%=67/344
[Paper]
Jiahao Cao, Kun Sun, Qi Li, Mingwei Xu, Zijie Yang, Kyung Joon Kwak, and Jason Li
In the 15th International Conference on Security and Privacy in Communication Networks (SecureComm)
Orlando, FL, USA, October 23-25, 2019
[Paper]
Jianhua Sun, Kun Sun, and Chris Shenefiel
In the 15th International Conference on Security and Privacy in Communication Networks (SecureComm)
Orlando, FL, USA, October 23-25, 2019
[Paper]
Jiahao Cao, Zijie Yang, Kun Sun, Qi Li, Mingwei Xu, and Peiyi Han
In the 22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID)
September 23-25, 2019
Acceptance ratio: 22.28%=37/166
[Paper]
Shengye Wan, Jianhua Sun, Kun Sun, Ning Zhang, and Qi Li
In the 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)
Portland, Oregon, June 24-27, 2019
Acceptance ratio: 21.40%=54/252
[Paper]
Xinda Wang, Kun Sun, Archer Batcheller, and Sushil Jajodia
In the 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)
Portland, Oregon, June 24-27, 2019
Acceptance ratio: 21.40%=54/252
[Paper]
Jiahao Cao, Qi Li, Renjie Xie, Kun Sun, Guofei Gu, Mingwei Xu, and Yuan Yang
In 28th USENIX Security Symposium (USENIX Security)
Santa Clara, CA, August 14-16, 2019
First round acceptance ratio: 9.8%=25/254
[Paper]
Shengye Wan, Yue Li, and Kun Sun
In CyberSecurity, Volume 2, number 1, February 20, 2019
Xin Lin, Yuewu Wang, Lingguang Lei, Jiwu Jing, Kun Sun, and Quan Zhou
In 2018 Annual Computer Security Applications Conference (ACSAC)
San Juan, Puerto Rico, December 3-7, 2018
Acceptance ratio: 20.1%=60/299
[Paper]
Kyle Wallace, Gang Zhou, and Kun Sun
In the 38th IEEE International Conference on Distributed Computing Systems (ICDCS)
Vienna, Austria, July 2-5, 2018
[Paper]
Ning Zhang, Ruide Zhang, Kun Sun, Wenjing Lou, Tom Hou, and Sushil Jajodia
In IEEE Transactions on Information Forensics and Security (TIFS), vol 13, no 9, pp 2345-2358
September 2018
Ning Zhang, Kun Sun, Deborah Shands, Wenjing Lou, and Thomas Hou
In IEEE International Conference on Computer Communications (INFOCOM)
Honolulu, HI, April 15-19, 2018
Acceptance ratio: 19.2%=309/1,606
[Paper]
Yue Li, Haining Wang, and Kun Sun
In IEEE International Conference on Computer Communications (INFOCOM)
Honolulu, HI, April 15-19, 2018
Acceptance ratio: 19.2%=309/1,606
[Paper]
Lingguang Lei, Yi He, Kun Sun, Jiwu Jing, Yuewu Wang, Qi Li, and Jian Weng
In the 24th ACM Conference on Computer and Communications Security (CCS)
Dallas, Texas, October 30-November 3, 2017
Acceptance ratio: 18%=151/836
[Paper]
Yue Li, Haining Wang, and Kun Sun
In the International Conference on Security and Privacy in Communication Networks (SECURECOMM)
Niagara Falls, CANADA, October 22-25, 2017
Acceptance ratio (full paper): 29.5%=31/105
[Paper]
Yi He, Qi Li, and Kun Sun
in the International Conference on Security and Privacy in Communication Networks (SECURECOMM)
Niagara Falls, CANADA, October 22-25, 2017
Acceptance ratio (full paper): 29.5%=31/105
[Paper]
Jiahao Cao, Mingwei Xu, Qi Li, Kun Sun, Yuan Yang, and Jing Zheng
In the International Conference on Security and Privacy in Communication Networks (SECURECOMM)
Niagara Falls, CANADA, October 22-25, 2017
Acceptance ratio (full paper): 29.5%=31/105
[Paper]
Jianhua Sun, Kun Sun, and Qi Li
In IEEE Conference on Communications and Network Security (CNS)
Las Vegas, NV,October 9-11, 2017
Acceptance ratio: 29.99%=41/137
[Paper]
Yue Li, Haining Wang, and Kun Sun
In IEEE Transactions on Information Forensics and Security (TIFS) page 2320-2333, Vol 12, Issue 10
October 2017
Lingguang Lei, Jianhua Sun, Kun Sun, Chris Shenefiel, Rui Ma, Yuewu Wang, and Qi Li
In the 14th Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA)
Bonn, Germany, July 6-7 2017
Acceptance ratio: 26.86%=18/67
[Paper]
Yacong Gu, Kun Sun, Purui Su, Qi Li, Yemian Lu, Lingyun Ying, and Denguo Feng
In the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)
Denver, CO, June 26-29, 2017
Acceptance ratio: 22.27%=49/220
[Paper]
Shengye Wan, Yue Li, and Kun Sun
In the IEEE ICC 2017, Communication and Information Systems Security Symposium
Paris, France, 2017
[Paper]
Yue Li, Nan Zheng, Haining Wang, Kun Sun, and Hui Fang
In the IEEE ICC 2017, Communication and Information Systems Security Symposium
Paris, France, 2017
[Paper]
Gangwon Hyun, Kun Sun, and Peng Ning
In Computer Communications, 104, 191-203
May 2017
Kyle Wallace, Kevin Moran, Ed Novak, Gang Zhou, and Kun Sun
In the IEEE Internet of Things Journal, vol 3, no 6, pp 1189-1201
December 2016.
Luren Wang, Yue Li, and Kun Sun
in the 36th IEEE International Conference on Distributed Computing Systems (ICDCS)
Nara, Japan, June 27-30, 2016
Acceptance ratio: 17.62%=68/386
[Paper]
Ning Zhang, Kun Sun, Wenjing Lou, and Tom Hou
in the 37th IEEE Symposium on Security and Privacy (S&P)
San Jose, CA, USA, MAY 23-25, 2016
Acceptance ratio: 13.75%=55/400
[Paper]
Chong Guan, Kun Sun, Zhan Wang, and Wen Tao Zhu
in the 11th ACM Symposium on Information, Compute rand Communications Security (ASIACCS)
Xi'an, China, May 30 June 3, 2016
Acceptance ratio: 20.9%=73/350 (full paper)
[Paper]
Yue Li, Haining Wang, and Kun Sun
in IEEE International Conference on Computer Communications (INFOCOM)
San Francisco, CA, April 10-15, 2016
Acceptance ratio: 18.25%=300/1,644
[Paper]
Jianhua Sun and Kun Sun
In IEEE International Conference on Computer Communications (INFOCOM)
San Francisco, CA, April 10-15, 2016
Acceptance ratio: 18.25%=300/1,644
[Paper]
Ning Zhang, He Sun, Kun Sun, Wenjing Lou, and Thomas Hou
In the 1st IEEE European Symposium on Security and Privacy (EuroS&P)
Saarbrücken, GERMANY, March 21-24, 2016
Acceptance ratio: 17.26%=29/168
[Paper]
Andrew Clark, Kun Sun, Linda Bushnell, and Radha Poovendran
in the Sixth Conference on Decision and Game Theory for Security (GameSec)
London, UK, on November 4-5, 2015
Acceptance ratio: 43.24%=16/37 (full papers)
[Paper]
He Sun, Kun Sun, Yuewu Wang, and Jiwu Jing
In Information Forensics and Security, IEEE Transactions on (TIFS), vol.10, no.12, pp.2547-2561
December 2015
He Sun, Kun Sun, Yuewu Wang, and Jiwu Jing
In the 22nd ACM Conference on Computer and Communications Security (CCS)
Denver, Colorado, October 12-16, 2015
Acceptance ratio: 19.81%=128/646
[Paper]
Xing Gao, Dachuan Liu, Haining Wang, and Kun Sun
In the 34th Symposium on Reliable Distributed Systems (SRDS)
Montreal, Canada, September 28 - October 01, 2015
Acceptance ratio: 29.63%=24/81 (regular papers)
[Paper]
He Sun, Kun Sun, Yuewu Wang, Jiwu Jing, and Haining Wang
In the 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)
Rio de Janeiro, Brazil, June 22-25, 2015
Acceptance ratio: 21.83%=50/229
[Paper]
Fengwei Zhang, Kevin Leach, Angelos Stavrou, HainingWang, and Kun Sun
In the 36th IEEE Symposium on Security and Privacy (S&P)
Fairmont, San Jose, CA, May 18-20, 2015
Acceptance ratio:13.51%=55/407
[Paper]
Ning Zhang, Kun Sun,Wenjing Lou, Y Thomas Hou, and Sushil Jajodia
In the 10th ACM Symposium on Information, Compute rand Communications Security (ASIACCS)
Singapore, April 14-17, 2015
Acceptance ratio: 17.84%=48/269 (full paper)
[Paper]
Xueqiang Wang, Kun Sun, Yuewu Wang, and Jiwu Jing
In the 22nd Annual Network & Distributed System Security Symposium (NDSS)
San Diego, California, February 2015
Acceptance ratio: 16.88%=51/302
[Paper]
He Sun, Kun Sun, Yuewu Wang, Jiwi Jing, and Sushil Jajodia
In the Proceedings of 18th European Symposium on Research in Computer Security (ESORICS)
Wroclaw, Poland, September 7-11, 2014
Acceptance ratio: 24.78%=58/234
[Paper]
Xingjie Yu, Zhan Wang, Kun Sun, Wen Tao Zhu, Neng Gao, and Jiwu Jing
In the 9th ACM Symposium on Information, Computer and Communications Security (ASIACCS)
Kyoto, Japan, June 4-6, 2014
Acceptance ratio: 19.60%=50/255 (short paper)
[Paper]
Fengwei Zhang, Jiang Wang, Kun Sun, and Angelos Stavrou
in IEEE Transactions on Dependable and Secure Computing (TDSC), vol.11, no.4, pp.332,344
July-Aug 2014
[Paper]
Rui Zhao, Chuan Yue, and Kun Sun
In Proceedings of the 5th ASE/IEEE International Conference on Information Privacy, Security, Risk and Trust (PASSAT)
Alexandria, VA, September 2013
[Paper]
Andrew W Clark, Kun Sun, and Radha Poovendran
In the 52nd IEEE Conference on Decision and Control (CDC)
Florence, Italy, December 10-13, 2013
[Paper]
Massimiliano Albanese, Alessandra De Benedictisy, Sushil Jajodia, and Kun Sun
In the First IEEE Conference on Communications and Network Security (CNS)
Washington D.C., USA, October 14-16, 2013
Acceptance ratio: 28.36%=40/141
[Paper]
Zhan Wang, Kun Sun, Sushil Jajodia, and Jiwu Jing
In the 27th IFIP WG 11.3 Conference on Data and Applications Security and Privacy (DBSEC)
Rutgers University, Newark, NJ, USA, July 15-17, 2013
Acceptance ratio: 35.55%=16/45 (full paper)
[Paper]
Quan Jia, Kun Sun, and Angelos Stavrou
In the International Conference on Computer Communications and Networks (ICCCN)
Nassau, Bahamas, 2013
Acceptance ratio: 28.66%=86/300 (regular paper)
[Paper]
Fengwei Zhang, Kevin Leach, Kun Sun, and Angelos Stavrou
In the 43rd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) Budapest, June 2013
Acceptance ratio: 20.90%=46/220
[Paper]
Xiaowei Mei, Donggang Liu, Kun Sun, and Dingbang Xu
In the 27th IEEE International Parallel & Distributed Processing Symposium (IPDPS>)
Boston, Massachusetts, May 2013
Acceptance ratio: 21.45%=106/494
[Paper]
Brian Schulte, Haris Andrianakis, Kun Sun ,and Angelos Stavrou
In the 9th Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA)
Heraklion, Crete, Greece, July 26-27th, 2012
Acceptance ratio: 31.81%=14/44
[Paper]
Jiang Wang, Kun Sun, and Angelos Stavrou
In the Proceedings of the 42nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN)
Boston, Massachusetts, June 2012
Acceptance ratio: 21.61%=51/236
[Paper]
Kun Sun, Jiang Wang, Fengwei Zhang, and Angelos Stavrou
In the Proceedings of the 19th Annual Network & Distributed System Security Symposium (NDSS)
San Diego, California, 5-8 February 2012
Acceptance ratio: 17.82%=46/258
[Paper]